Alternatives to Proof of Work
 Decentalization of blockchain transactions does not require a central authority to approve users' transactions on the blockchain. Different people are, instead, trusted to approve these transactions honestly to avoid problems such as Double Spending where a user who approves his or her own blocks could spend his or her coins twice by first authorizing two transactions and then successfully approving blocks quickly before the rest of users involved in the same transaction can approve it. The different people who approve blocks in blockchains are incentivized by a reward with some of the network's cryptos, part of the transaction fees or crypto created from scratch. However, a system that requires many different people to approve transactions or blocks is just a simple solution to problems eminent in blockchain-based transactions. For instance, one user could also create many false identities that would then be used to approve all the blocks in which his or her specific created transactions (that are meant to achieve double spending), are. This is called Sybil Attack. The attack is prevented by adding cost to approving of these blocks such that it is not easy for a single user to create new identities and use them to approve blocks for his or her transactions. Proof of Work was created to add costs of approving each block such that it discourages a person from creating multiple fake identities and using them to approve their own transactions. In this case, the user is required to do some computational work to sign off on a block since the user cannot fake computational work. However, this system has a number of problems such as high consumption of power and low efficiency as we will see later, which resulted to creating of alternatives such as Proof of Work, Proof of Stake, Proof of Cooperation, Proof of Burn, Proof of Activity and Proof of Importance.
Decentalization of blockchain transactions does not require a central authority to approve users' transactions on the blockchain. Different people are, instead, trusted to approve these transactions honestly to avoid problems such as Double Spending where a user who approves his or her own blocks could spend his or her coins twice by first authorizing two transactions and then successfully approving blocks quickly before the rest of users involved in the same transaction can approve it. The different people who approve blocks in blockchains are incentivized by a reward with some of the network's cryptos, part of the transaction fees or crypto created from scratch. However, a system that requires many different people to approve transactions or blocks is just a simple solution to problems eminent in blockchain-based transactions. For instance, one user could also create many false identities that would then be used to approve all the blocks in which his or her specific created transactions (that are meant to achieve double spending), are. This is called Sybil Attack. The attack is prevented by adding cost to approving of these blocks such that it is not easy for a single user to create new identities and use them to approve blocks for his or her transactions. Proof of Work was created to add costs of approving each block such that it discourages a person from creating multiple fake identities and using them to approve their own transactions. In this case, the user is required to do some computational work to sign off on a block since the user cannot fake computational work. However, this system has a number of problems such as high consumption of power and low efficiency as we will see later, which resulted to creating of alternatives such as Proof of Work, Proof of Stake, Proof of Cooperation, Proof of Burn, Proof of Activity and Proof of Importance.
Understanding Proof of Work
 For starters, Proof of Work is an economic measure to deter denial of service, spam and other service abuses and interruption by requiring that the user or miner performs some work such as working out math problems and the system checking if the solutions or answers are correct to approve access. In the real world sense, it takes real-world resources to work out these solutions, which is translated to mean computer processing time and computer processing power. In other words, in Proof of Work, calculations are needed by the network nodes to form a distributed ledger (the system that keeps track of wallets involved in a transaction, amount these wallets have, and history of activity on the wallets) needed for mining. The real-world resources in this case are computers and electricity, and that's where the problem of POW lies. In other words, computers or clusters of computers spend a lot of electricity power and time when calculating potential solutions, which mean miners have high energy costs to cope with in the end. The problem actually reduces the number of miners on networks. Proof of Work has another problem: it is possible for a miner or a mining pool to own 51 percent of the network's computational power, leading to the 51 percent attack – a situation where the miner creates and confirms their own fraudulent blocks so quickly in a way that invalidates genuine blocks and valid transactions from other miners of the community. An example of coins that use this system is Bitcoin.
For starters, Proof of Work is an economic measure to deter denial of service, spam and other service abuses and interruption by requiring that the user or miner performs some work such as working out math problems and the system checking if the solutions or answers are correct to approve access. In the real world sense, it takes real-world resources to work out these solutions, which is translated to mean computer processing time and computer processing power. In other words, in Proof of Work, calculations are needed by the network nodes to form a distributed ledger (the system that keeps track of wallets involved in a transaction, amount these wallets have, and history of activity on the wallets) needed for mining. The real-world resources in this case are computers and electricity, and that's where the problem of POW lies. In other words, computers or clusters of computers spend a lot of electricity power and time when calculating potential solutions, which mean miners have high energy costs to cope with in the end. The problem actually reduces the number of miners on networks. Proof of Work has another problem: it is possible for a miner or a mining pool to own 51 percent of the network's computational power, leading to the 51 percent attack – a situation where the miner creates and confirms their own fraudulent blocks so quickly in a way that invalidates genuine blocks and valid transactions from other miners of the community. An example of coins that use this system is Bitcoin.
Enter alternatives
Proof of Stake
 Proof of Stake exists to solve these or some of these problems. It originated in the Bitcointalk in 2011 and first applied on Peercoin. It requires that a miner locks up some of the amount of their coins to verify their blocks of transactions. In other words, you are only required to verify (and stake) a certain percentage of the coins available in a given currency in order to verify a block of transactions. For instance, you are allowed to mine 2 percent of all transactions across Ethereum if you own 2 percent of all Ether. This way, the method requires cryptography calculations that are easy for computers to solve. With PoS, those with more coins are able to mine more blocks. It does not need electricity and hardware beyond what is normal, and is efficient thus encouraging more people to run nodes. PoS also helps take computational power out of the hands of few miners and GPU farms that are doing the bulk of mining, to distribute it evenly across the network. This leads to a more democratized system and augurs well with the ideas of decentralization as promoted by various cryptos. - Randomized block selection: Nodes predict the stake (among all public stakes) that creates the next block by using an algorithm that looks for the lowest hash value in combination with the size of the stake. Nxt coin and Black coin use this method. - Coin age selection: In this case, the age (measured in days) of the coin is calculated by multiplying the number of sent coins with the average age on the coins. The age resets to zero when a coin is sent and when it provides its signature. Unspent coins wait for 30 days before competing to create the next block. Stakers are rewarded by creating new coins, which is done by way of forging – recycling transaction fees, or minting – inflating the current supply. Examples of coins using this method are Novacoin and Peercoin. However, it has another problem, called the “problem of nothing at stake” and is not ideal for a distributed consensus protocol. The problem of nothing at stake is solved through the variations of Proof of Stake methods: - Proof of Stake Anonymous (PoSA): It was introduced by http://www.cloakcoin.com/ and involves some users clocking transactions to aid in the anonymization of the blockchain transactions (these users are rewarded for it). Some other users give inputs and outputs that help in identifying the source and destination of the transaction. - Delegated Proof of Stake (DPoS): It was first seen by Bitshares blockchain and involves users voting for delegates who are given the power to earn profit from running a full node. It helps prevent users from unwanted regulatory interference. - Proof of Importance (POI): This method was first introduced by NEM coin. Accounts are given importance based on their importance to the economy (the method was introduced to promote economic activity) and these are able to harness and harvest rewards. It prevents users from spending coins they do not have. - Proof of Storage: First formulated in 2013 and used by Storj coin, it uses a blocktree instead of blockchain and users see only the transactions relevant to them. Each node on the blocktree has a blockchain. This method is related to Proof of Capacity in working, but the space designated is used by all participants as common cloud storage. - Proof of Stake Time (PoST): First used by Vericoin, the method uses coin age, but the age is calculated using the period of time coins were held at the address in question. Many Proof of Stake methods target at making the rich richer and this method was meant to solve that problem. - Proof of Stake Velocity (PoSV): It was first used by Reddcoin and users are rewarded according to the amount of coins they have and how active they use them.
Proof of Stake exists to solve these or some of these problems. It originated in the Bitcointalk in 2011 and first applied on Peercoin. It requires that a miner locks up some of the amount of their coins to verify their blocks of transactions. In other words, you are only required to verify (and stake) a certain percentage of the coins available in a given currency in order to verify a block of transactions. For instance, you are allowed to mine 2 percent of all transactions across Ethereum if you own 2 percent of all Ether. This way, the method requires cryptography calculations that are easy for computers to solve. With PoS, those with more coins are able to mine more blocks. It does not need electricity and hardware beyond what is normal, and is efficient thus encouraging more people to run nodes. PoS also helps take computational power out of the hands of few miners and GPU farms that are doing the bulk of mining, to distribute it evenly across the network. This leads to a more democratized system and augurs well with the ideas of decentralization as promoted by various cryptos. - Randomized block selection: Nodes predict the stake (among all public stakes) that creates the next block by using an algorithm that looks for the lowest hash value in combination with the size of the stake. Nxt coin and Black coin use this method. - Coin age selection: In this case, the age (measured in days) of the coin is calculated by multiplying the number of sent coins with the average age on the coins. The age resets to zero when a coin is sent and when it provides its signature. Unspent coins wait for 30 days before competing to create the next block. Stakers are rewarded by creating new coins, which is done by way of forging – recycling transaction fees, or minting – inflating the current supply. Examples of coins using this method are Novacoin and Peercoin. However, it has another problem, called the “problem of nothing at stake” and is not ideal for a distributed consensus protocol. The problem of nothing at stake is solved through the variations of Proof of Stake methods: - Proof of Stake Anonymous (PoSA): It was introduced by http://www.cloakcoin.com/ and involves some users clocking transactions to aid in the anonymization of the blockchain transactions (these users are rewarded for it). Some other users give inputs and outputs that help in identifying the source and destination of the transaction. - Delegated Proof of Stake (DPoS): It was first seen by Bitshares blockchain and involves users voting for delegates who are given the power to earn profit from running a full node. It helps prevent users from unwanted regulatory interference. - Proof of Importance (POI): This method was first introduced by NEM coin. Accounts are given importance based on their importance to the economy (the method was introduced to promote economic activity) and these are able to harness and harvest rewards. It prevents users from spending coins they do not have. - Proof of Storage: First formulated in 2013 and used by Storj coin, it uses a blocktree instead of blockchain and users see only the transactions relevant to them. Each node on the blocktree has a blockchain. This method is related to Proof of Capacity in working, but the space designated is used by all participants as common cloud storage. - Proof of Stake Time (PoST): First used by Vericoin, the method uses coin age, but the age is calculated using the period of time coins were held at the address in question. Many Proof of Stake methods target at making the rich richer and this method was meant to solve that problem. - Proof of Stake Velocity (PoSV): It was first used by Reddcoin and users are rewarded according to the amount of coins they have and how active they use them.
Proof of Activity

Proof of Activity combines both Proof of Work and Proof of Stake in that a blockchain includes the both types of blocks. The system acts as an accounting such that it checks the total complexity of work.
In this case, Proof of Work serves as a honest emission while Proof of Stake works more like an annual deposit income.
A miner uses the Proof-of-Work to search for a hash that conforms to the complexity. After the hash is found, data is transmitted to the network to form a block template that is yet to become a block. That block hash is interpreted as hash numbers each corresponding to satoshi, each of which corresponds to a single public key corresponding to a particular single owner.
Therefore, N public keys on the block correspond to N owners who must sign the block template for it to become a block. If a miner is not available, new templates keep forming with different sets of signers candidates as Proof of Work miners keep working. One block will eventually be signed N times and the reward on it is shared between proof-of-work-miner and N signers.
Proof-of-Checkpoint
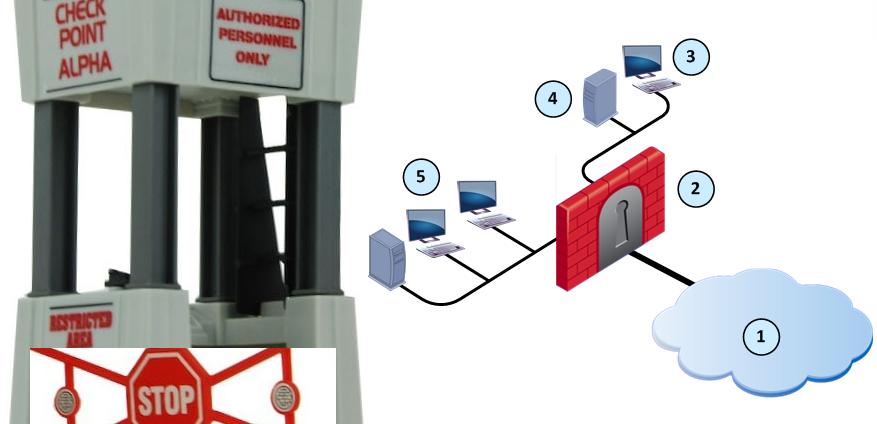
This method uses both Proof of Stake and Proof of Work methods. It seeks to migrate attacks on the Proof of Stake system, but it is possible that a node can be attacked if it has been offline for an extended period -- it can then be used to provide false information about the blockchain.
In this method, A Proof of Work block is required to mine x amount of blocks on the Proof of Stake systems. Each Proof of Work block has no transactions and is linked to both the Proof of Work network and the Proof of Stake network.
Proof of Burn

Proof of Burn alternative to Proof of Work and Proof of Stake. It requires that you proof having burned some digital coins instead of proofing burning electricity like is the case with Proof of Work. The proof is accomplished by sending the coins to addresses or an address from where they cannot be redeemed. This is throwing coins away, literally because you for instance send the coins to some address with a hash of a random number because the chances are rare or negligible that someone will pick public and private keys for it.
You get the rights for life-time-mining in exchange with throwing away the coins. The more you throw away, the more your chances. Thus, it works like buying a virtual Proof-of-Work hardware that will not degrade or a Proof of Stake you cannot get back. Definitely, it works well with mature period compared to the early stage of cryptocurrency evolution.
Proof of Capacity
Also known as Proof of Space, Proof of Capacity method relies on using more megabytes as resources where the algorithm allocates a significant volume of hard drive space on the user machine in order for the user to start mining.
It is more energy efficient than Proof of Work and achieves botnet protection since it is hard to install a miner on victim's PC to steal a couple terabytes. For this method, the algorithm repeatedly hashes your public key and nonces such that each of your megabyte is an additional lottery ticket in mining.
Proof of Cooperation

Proof of Cooperation uses Cooperatively Validated Nodes (CVNs) to generate the transaction blocks and they cooperate to maintain network security. There is no mining or minting systems. The method was recently announced by Faircoin 2 and all 53.193.831 Faircoin in circulation were transferred to the new system on 18th July this year.
In the Faircoin system, various tools that can be shared by users are created -- they include point of sale systems for merchants, prepaid cards, instant currency exchange, exchanges to euros via ATMs, payment of direct receipts and all the banking services. It helps lower computation power and electricity as well as distributing the power from a few users to many users.
The machines search for and validate transactions in a rotating form and in turn receive a small reward as a "thanks" for the cooperation and for the energy they use.
Proof of Membership (PoM)

Proof of Membership method limits, economically, creation of minting accounts in the primary market and discourages selling coins in a secondary market. It uses two different tokens: minter accounts and currency units (coins). Minter accounts are the only ones that create a block but the rate of creation is limited by a set amount of new accounts for each block. The accounts can be sold but only at the time of creation, so the seller will not know the private key to steal funds back
It adds security of the system by increasing the economic costs of an attack, which is achieved by making accounts expensive. Making accounts expensive also discourages the 51% attacks because one would require more time and resources to buy and control that amount of transactions. Owners of these accounts get rewarded by a free account whenever they create a block in the blockchain, and they can invite new users to these accounts free of charge. Any user can also create a free account in the system although free accounts do not enjoy the same privileges as expensive accounts.
Proof of Existence

Proof of Existence uses timestamped transactions in the blockchain to verify that computer files actually existed or exist as of a particular time.
Proof of Play

Unlike Proof of Work scheme where one must do difficult computations and work to secure and approve coin transactions and get rewarded, Proof of Play requires a player to do cognitive workload -- playing a 2D motorbike simulation game to mine the coin -- to earn coins, meaning the algorithm utilizes human skill and manual input to mine instead of computing power. The first coin to use that is Motocoin although Huntercoin also uses this algorithm.
This algorithm is in-built and allows the game to fund itself such that the rewards are lowered as time goes. A percentage of the currency mined in-game goes to developers through NPC purchases.
In Huntercoin, user's events are recorded in their respective blockchain and the user's client runs through the blockchain to learn what moves the user has made. The player collects huntercoins on the map, and these coins can be brought to a spawn area and redeemed in the user's wallet, then used to create new Hunters or like any other cryptos.


